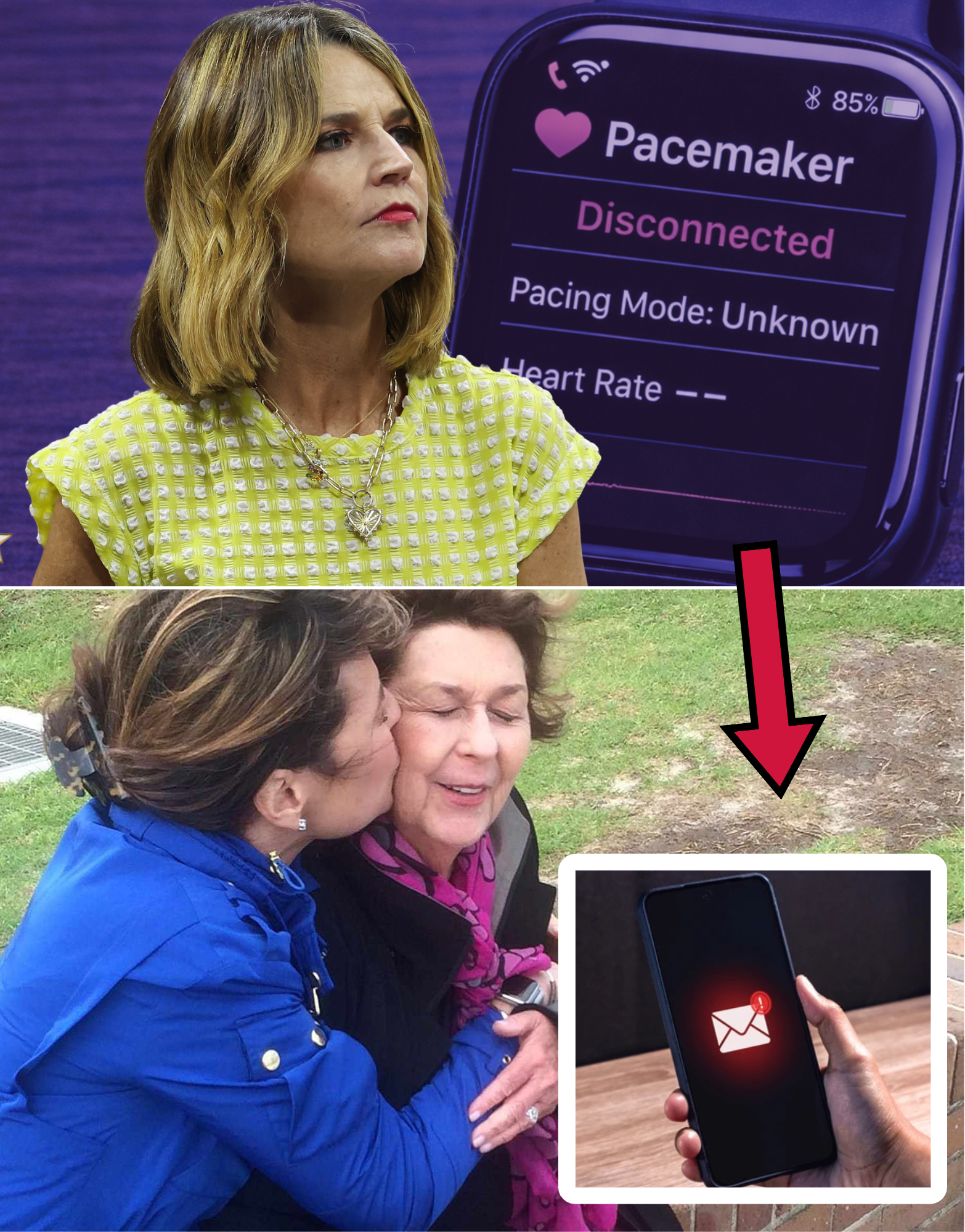
At exactly 2:28 a.m. on February 1, 2026, the remote monitoring system for Nancy Guthrie’s pacemaker recorded an abrupt and unexplained loss of connection with her paired smartphone. The automated alert, sent to her healthcare provider and family-linked accounts, signaled that the 84-year-old’s implanted cardiac device had stopped transmitting real-time data—a critical lifeline for managing her arrhythmia and heart conditions. Within minutes of that digital silence, an anonymous email landed in a family member’s inbox, its arrival so precisely timed that investigators now consider it inseparable from the abduction that unfolded in the pre-dawn darkness at her Catalina Foothills home in Tucson, Arizona.
The email—subject line and full content partially withheld to safeguard the investigation—contained a short, cryptic message that implied awareness of Nancy Guthrie’s current state and whereabouts. Law enforcement sources familiar with the communication describe it as calculatedly ambiguous yet unmistakably threatening: no explicit ransom demand, but clear insinuation of control and menace. Sent from a freshly created, disposable account routed through layered anonymizing proxies, the message evaded immediate tracing but left digital breadcrumbs that FBI cyber experts are aggressively pursuing—header analysis, IP chain reconstruction, server logs, and embedded metadata that could expose the sender’s location or identity.
The pacemaker disconnection is far from a routine technical glitch. Nancy Guthrie depended on the device for continuous heart rhythm regulation and took daily medications for hypertension and related cardiac issues. The sudden cutoff—without power outage at the residence, device battery failure, or any prior warning—points strongly to deliberate interference: her phone was either powered down, destroyed, removed from proximity, or forcibly unpaired during the attack. This timeline dovetails with the known sequence of events captured on residual doorbell camera data and corroborated by nearby dashcam footage.
Around 1:47 a.m., the Google Nest doorbell camera was first tampered with: a masked, armed suspect—dressed head-to-toe in dark clothing, backpacked, and with a holstered handgun—tilted his head to avoid the lens, raised a gloved hand to block or adjust the device, then gathered yard branches and leaves to obscure it. When that failed to fully blind the camera, he fired a single shot at close range to shatter the unit completely. Physical evidence at the scene includes scattered fragments, bullet impact marks, and Nancy Guthrie’s confirmed blood on the porch. Between that destruction and the 2:28 a.m. pacemaker alert, the intruder likely completed the abduction—removing her phone, forcing her out of the house, and leaving behind her wallet, hearing aid, medications, and vehicle.
The anonymous email’s arrival shortly after the disconnection suggests either real-time monitoring of the situation or immediate follow-up by someone with detailed knowledge of the events. Possibilities under active investigation include: the sender had physical access to the phone during the crime, used spyware or tracking software already installed, or coordinated with the intruder to send the message as part of a psychological or extortion strategy. The FBI’s cyber unit is working to authenticate the email’s origin, rule out spoofing, and trace any overlapping digital footprints with the suspect’s actions at the residence.
Forensic teams continue expedited processing of touch DNA lifted from the destroyed doorbell housing, mounting bracket, porch railings, scattered fragments, and the flashlight the suspect clenched in his mouth—potentially yielding saliva traces. These biological samples are being fast-tracked for lab analysis and database cross-referencing. Behavioral experts, including former FBI officials like Chris Swecker, have noted the intruder’s composure in the footage: unhurried movements, tactical efficiency, and apparent familiarity with the property layout, suggesting possible prior reconnaissance. Swecker warned that public release of the video likely shifted the suspect from calm to anxious: “Now that it’s out there, he’s probably feeling the heat.”
The family’s public statements reflect deepening anguish and determination. Savannah Guthrie’s most recent solo appeal was raw and urgent: “We are at an hour of desperation. We need your help. Bring her home.” She called on anyone nationwide to report even the smallest detail, emphasizing that distance from Tucson does not diminish the value of a tip. Earlier family videos addressed presumed captors directly, evolving from hopeful pleas (“We are ready to listen”) to acknowledgment of possible communications (“We received your message, and we understand”). Ransom notes sent to media outlets carried expired deadlines without verified proof of life or authenticated contact; authorities continue treating all communications—including the anonymous email—as live investigative material.
The neighborhood’s physical characteristics—dense foliage, large lot setbacks, privacy hedges—have hindered additional surveillance recovery. Residents report common gaps: most private cameras cover only immediate yards, not streets or sidewalks. One neighbor stated: “Our cameras only see the front yard, not the street, because of the distance… And that’s not rare here.” Late-night activity (joggers, dog walkers at 10–11 p.m.) is routine in this “very safe” community, amplifying the shock of the crime’s boldness.
Digital billboards flash alerts across states, neighborhood canvassing expands including near daughter Annie Guthrie’s home, and the tip line (1-800-CALL-FBI) remains active. The pacemaker alert at 2:28 a.m. and the near-immediate anonymous email create a razor-sharp timeline that demands explanation. Whether the sender monitored the disconnection live, had post-abduction access to the phone, or coordinated the message as part of a larger plan, the precision points to sophistication and intent.
As cyber teams chase the email’s trail and forensics process every surface the intruder touched, time presses critically for an elderly woman without her medications or pacemaker oversight. The neighborhood once proud of its seclusion now grapples with how privacy became peril. The nation watches, hoping one digital trace, overlooked clue, or panicked error ends this nightmare. For Savannah Guthrie and her family, the plea remains simple, urgent, and unbreakable: “Bring her home.”

